Proper Authentication is required?

Proper authentication is a key security requirement when accessing resources via a network, username/password is no more sufficient!
Various secure authentication methods are implemented by ApplicGate such as:
- Certificates
- One-Time Password (OTP)
- Time-based One-Time Password (TOTP)
- OAuth 2.0
- Web Authentication (WebAuthn), FIDO2

Use Cases/TechInfo
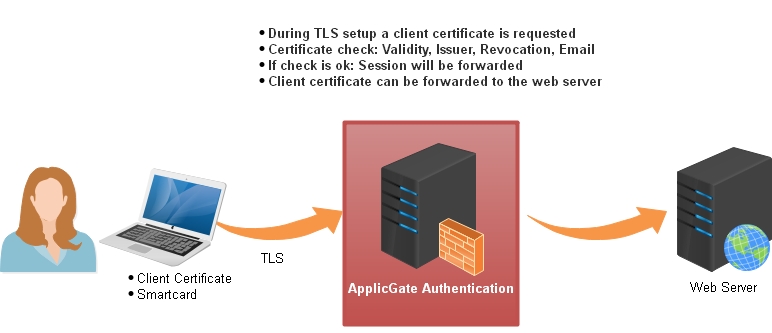
Certificates
You can use any certificate (software certificate or smartcard) for authentication.
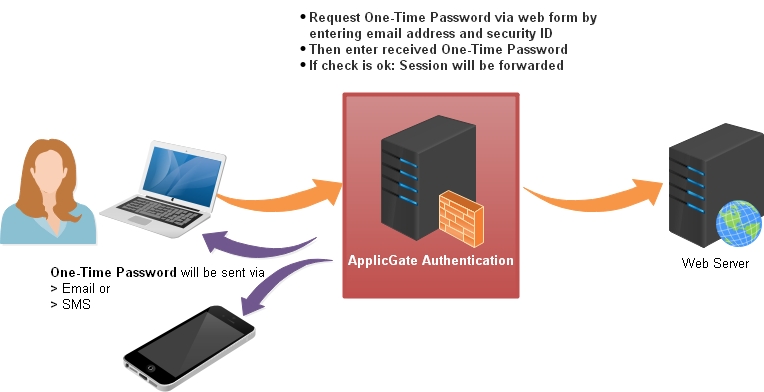
One-Time Password (OTP)
You have to enter a One-Time Password that has been set to you via SMS or email.
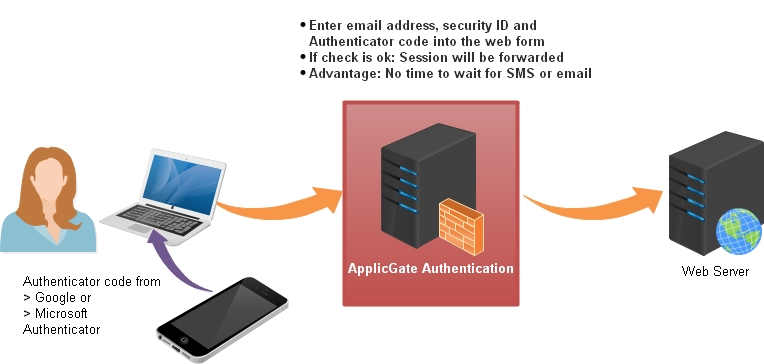
Time-based One-Time Password (TOTP)
You have to enter the code generated by Google or Microsoft Authenticator. (Initial authentication is done via SMS or email.)
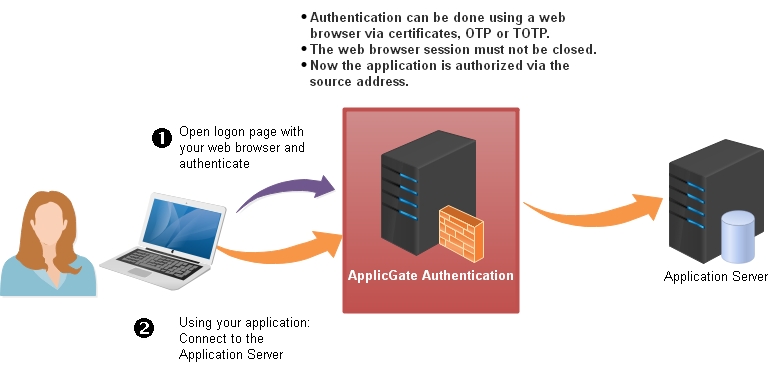
Logon to ApplicGate
Use this feature for additional authentication for protocols other than https, e.g. RDP. Authentication by certificates, OTP and TOTP is supported.
FAQ + Techblog
Q: Is ApplicGate available for Linux also?
A: Yes, it is. Send an email to contact@applicgate.com and we will be glad to send you a version built for Linux.
How to tunnel UDP traffic over TCP
If you would like to secure UDP traffic via unsecure networks or network segments you can add authentication and encryption easily.