Secure Access Hub wanted?
ApplicGate offers network segmentation on application layer for industry and critical infrastructures.
Additional to layer 5 application routing the portable application for Windows and Linux enables control of load-balancing and logging for IPv4 and IPv6 services.
- Implement complex network routing requirements with high security
- Control of data exchange and application provisioning
- Network segmentation on transport and session layer
- IP address und port translation for TCP/UDP protocols
- UDP tunneling via TCP (TLS)
- Failover configuration / load balancer for any TCP/UDP services
- Access control, session logging, audit log
- Security protocol router available for Linux und Windows

Use Cases/TechInfo
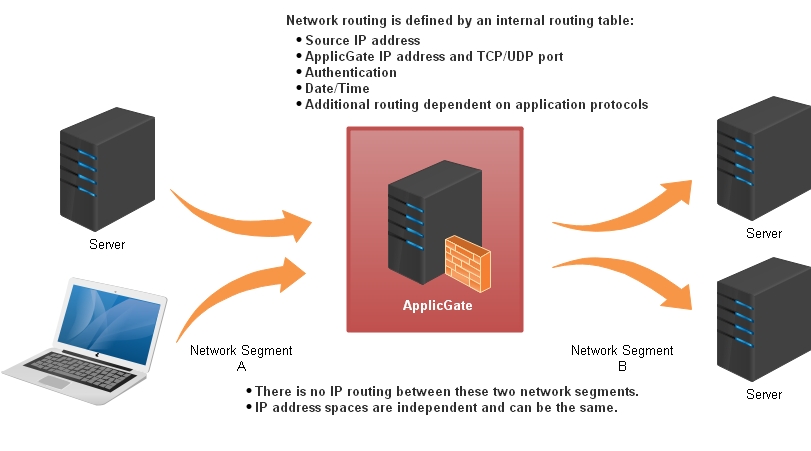
Network Segmentation
TCP/UDP connections terminate at ApplicGate and are routed to the destination according a routing table.
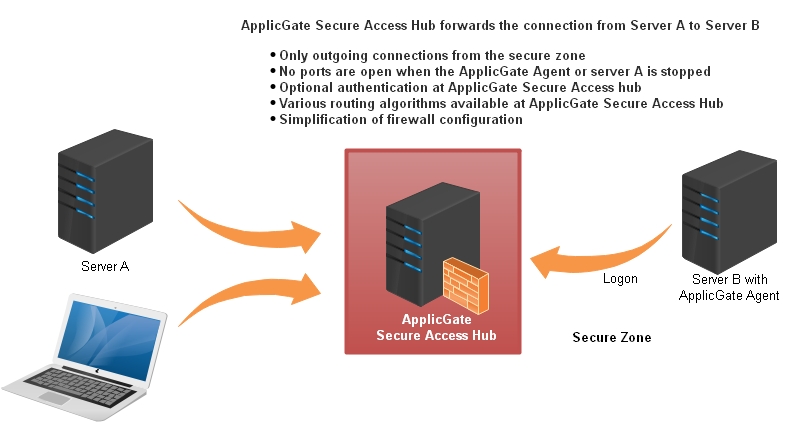
Reverse Connection Establishment
ApplicGate can be configured with only outgoing connections from servers.
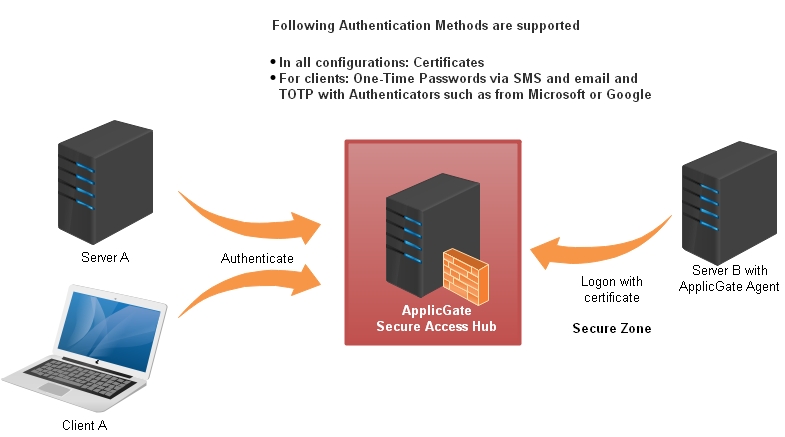
Additional Authentication
Various optional authentication methods can be configured.
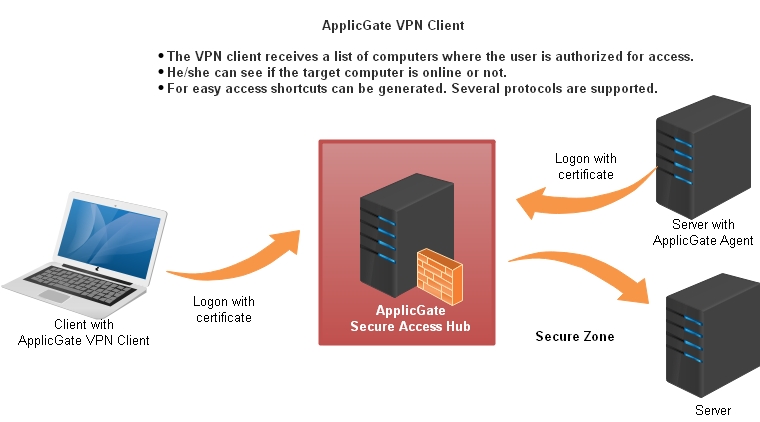
VPN Client
A VPN client can be easily downloaded via Click Once.
FAQ + Techblog
Q: Is ApplicGate available for Linux also?
A: Yes, it is. Send an email to contact@applicgate.com and we will be glad to send you a version built for Linux.
How to tunnel UDP traffic over TCP
If you would like to secure UDP traffic via unsecure networks or network segments you can add authentication and encryption easily.