Exchange Active Sync Gateway anyone?
Do you think that username/password is sufficient to access Exchange mailboxes by any device from everywhere in the Internet?
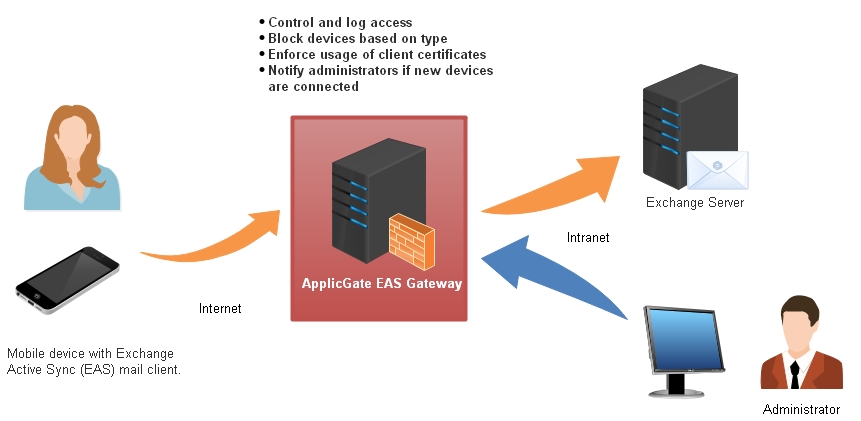
Resume control over your mobile devices (smartphones, tablets etc.) accessing your Exchange mail server via the Exchange Active Sync (EAS) protocol.
- Only identified devices are allowed to access the mail server.
- The users cannot change the client hardware without central permission.
- Additional authentication by certificates can be enforced.
- Monitoring and administration can be delegated.

Use Cases/TechInfo
Control Access
Monitor and control/restrict access from mobile devices (using the EAS protocol) to Exchange server mailboxes. No unidentified device is allowed to access the Exchange mailbox.
Log mobile Device Access
Get usage data of mobile devices.
Block Devices, Enforce client certificates
Unwanted mobile device types can be blocked. For mailboxes with high protection requirements the usage of client certificates can be enforced.
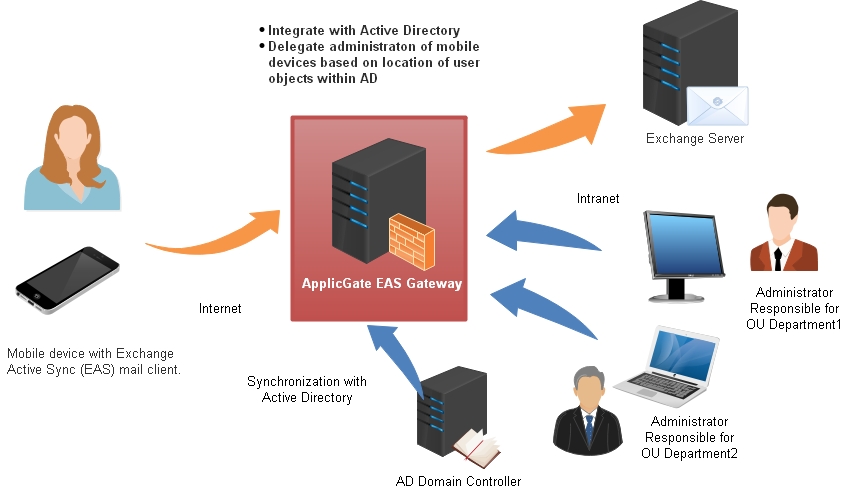
Active Directory Integration
Easy delegation of management rights via synchronization of the ApplicGate user database with Microsoft Active Directory (AD)
FAQ + Techblog
Q: Is ApplicGate available for Linux also?
A: Yes, it is. Send an email to contact@applicgate.com and we will be glad to send you a version built for Linux.
How to tunnel UDP traffic over TCP
If you would like to secure UDP traffic via unsecure networks or network segments you can add authentication and encryption easily.